Key Takeaways
- Foundational Knowledge: Gain essential insights into cybersecurity fundamentals, including encryption, authentication, and network security, to establish a strong foundation for protecting digital assets.
- Proactive Defense Strategies: Learn actionable strategies such as multi-factor authentication, intrusion detection, and incident response planning to proactively defend against cyber threats and mitigate risks effectively.
- Continuous Learning: Embrace a mindset of continuous learning and adaptation in the ever-evolving landscape of cybersecurity to stay ahead of emerging threats and safeguard personal and organizational security.
In an age where virtually every aspect of our lives intertwines with the digital realm, the significance of cybersecurity cannot be overstated.
From safeguarding personal data to protecting critical infrastructure, understanding the fundamentals of cybersecurity is no longer a luxury but an absolute necessity.
Welcome to our comprehensive guide: “Mastering Cybersecurity Basics: Understanding Key Concepts.”

As we embark on this journey through the intricate landscape of cybersecurity, it’s essential to recognize that the digital world is both a realm of boundless opportunity and an arena fraught with peril.
With every click, swipe, and keystroke, individuals and organizations alike expose themselves to a myriad of threats, ranging from insidious malware to sophisticated cyber-attacks.
Yet, amidst this ever-evolving digital landscape, empowerment lies in knowledge – knowledge of the fundamental principles that underpin cybersecurity defenses.
In this extensive exploration, we aim to equip you with the essential knowledge and tools to navigate the complexities of cybersecurity confidently.
Whether you’re a seasoned IT professional seeking to bolster your expertise or a novice user aiming to fortify your online defenses, this guide is tailored to meet your needs.
So, what exactly does it mean to master cybersecurity basics?
It’s about more than just memorizing technical jargon or implementing off-the-shelf solutions.
It’s about cultivating a deep understanding of the core concepts that form the bedrock of effective cybersecurity practices.
It’s about demystifying the terminology and unraveling the complexities to empower you to make informed decisions and take proactive measures to secure your digital assets.
Throughout this guide, we’ll embark on an enlightening journey through the following key concepts:
- Understanding Cybersecurity Fundamentals: We’ll delve into the very essence of cybersecurity, exploring its significance and core objectives. By grasping the foundational principles of cybersecurity, you’ll gain a newfound appreciation for its indispensable role in safeguarding data integrity, confidentiality, and availability.
- Exploring Threats and Vulnerabilities: From the nefarious world of malware to the deceptive tactics of phishing, we’ll shine a spotlight on the myriad threats lurking in cyberspace. By understanding the anatomy of cyber threats and vulnerabilities, you’ll be better equipped to identify, mitigate, and combat potential risks.
- Encryption and Cryptography: Step into the realm of encryption, where data is transformed into an impregnable fortress of unreadable ciphertext. We’ll demystify the inner workings of cryptographic algorithms and unveil the power of encryption in securing sensitive information against prying eyes.
- Authentication and Access Control: Journey into the realm of user authentication and access control, where identity verification reigns supreme. From passwords to biometrics, we’ll explore the various mechanisms employed to verify user identities and restrict access to authorized personnel only.
- Network Security Concepts: Take a deep dive into the realm of network security, where the battle for digital supremacy unfolds. We’ll unravel the mysteries of firewalls, intrusion detection/prevention systems, and virtual private networks (VPNs), equipping you with the knowledge to fortify your digital perimeters against intruders.
- Incident Response and Disaster Recovery: Prepare to navigate the turbulent waters of cyber incidents and data breaches with grace and resilience. We’ll outline the essential components of an effective incident response plan and illuminate the path to swift recovery and business continuity in the face of adversity.
By the time you reach the end of this guide, you’ll emerge not only with a newfound mastery of cybersecurity basics but also with the confidence and proficiency to tackle the myriad challenges of the digital age head-on.
So, without further ado, let’s embark on this transformative journey together and unlock the secrets to a safer, more secure digital future.
Before we venture further into this article, we like to share who we are and what we do.
About 9cv9
9cv9 is a business tech startup based in Singapore and Asia, with a strong presence all over the world.
With over eight years of startup and business experience, and being highly involved in connecting with thousands of companies and startups, the 9cv9 team has listed some important learning points in this overview of Understanding the Key Concepts of Cybersecurity.
If you are looking for a job or an internship, click over to use the 9cv9 Job Portal to find your next top job and internship now.
Mastering Cybersecurity Basics: Understanding Key Concepts
- Understanding Cybersecurity Fundamentals
- Exploring Threats and Vulnerabilities
- Encryption and Cryptography
- Authentication and Access Control
- Network Security Concepts
- Incident Response and Disaster Recovery
1. Understanding Cybersecurity Fundamentals
In the digital age, cybersecurity fundamentals serve as the cornerstone for protecting sensitive information and digital assets from malicious actors.
By comprehensively understanding these fundamentals, individuals and organizations can establish robust defenses against cyber threats. Let’s delve into the essential components of cybersecurity fundamentals:
The Significance of Cybersecurity
- Protection of Data Integrity: Cybersecurity ensures that data remains accurate, reliable, and unaltered by unauthorized parties.
- Confidentiality Assurance: It safeguards sensitive information from unauthorized access, ensuring that only authorized individuals can access confidential data.
- Availability Assurance: Cybersecurity measures aim to maintain the availability of data and systems, preventing disruptions that could lead to downtime or loss of productivity.
Example:
- Consider a financial institution that handles sensitive customer data. Implementing cybersecurity measures ensures that customer account information remains confidential, preventing unauthorized access and protecting the integrity of financial transactions.

Core Objectives of Cybersecurity
- Prevention: Proactive measures are taken to prevent cyber threats from exploiting vulnerabilities and infiltrating systems.
- Detection: Systems and networks are continuously monitored to detect any suspicious activity or unauthorized access attempts.
- Response: In the event of a cyber incident, swift and effective responses are initiated to mitigate the impact and prevent further damage.
- Recovery: Post-incident, recovery efforts focus on restoring systems to their normal functioning state and implementing measures to prevent future occurrences.
Example:
- An e-commerce platform implements firewalls and intrusion detection systems to prevent unauthorized access to customer data. In the event of a cyber attack, the platform’s incident response team swiftly identifies and contains the breach, minimizing the impact on customer transactions. Post-incident, the team conducts a thorough investigation to identify vulnerabilities and strengthens cybersecurity measures to prevent similar incidents in the future.
Importance in Safeguarding Personal and Organizational Data
- Personal Data Protection: Cybersecurity safeguards individuals’ personal information, such as financial data, medical records, and personal identifiers, from identity theft and fraud.
- Organizational Data Protection: For businesses and institutions, cybersecurity is crucial for protecting proprietary information, financial records, and intellectual property from theft or unauthorized access.
- Compliance Requirements: Adhering to cybersecurity best practices helps organizations comply with regulatory requirements and industry standards, such as GDPR, HIPAA, and PCI DSS.
Example:
- A healthcare organization is entrusted with sensitive patient data. Implementing robust cybersecurity measures not only protects patient confidentiality but also ensures compliance with regulatory standards such as HIPAA. By safeguarding patient records from data breaches and unauthorized access, the organization maintains trust with patients and avoids potential legal consequences.
Understanding cybersecurity fundamentals lays the groundwork for building resilient defenses against evolving cyber threats.
By prioritizing data integrity, confidentiality, and availability, individuals and organizations can mitigate risks, protect sensitive information, and uphold trust in the digital ecosystem.
Stay tuned as we delve deeper into essential cybersecurity concepts in the following sections.
2. Exploring Threats and Vulnerabilities
Understanding the landscape of cyber threats and vulnerabilities is paramount in fortifying digital defenses against malicious actors.
In this section, we’ll delve into the diverse array of threats and vulnerabilities that pose risks to individuals and organizations alike.
Common Cyber Threats
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems or networks.
- Examples include viruses, worms, Trojans, ransomware, and spyware.
- Phishing: Deceptive tactics used to trick individuals into divulging sensitive information, such as passwords or financial details, by posing as a trustworthy entity.
- Phishing attacks often occur via email, social media, or instant messaging platforms.
- Denial-of-Service (DoS) Attacks: Attempts to overwhelm a network, server, or website with a flood of traffic, rendering it inaccessible to legitimate users.
- Distributed Denial-of-Service (DDoS) attacks involve multiple compromised devices (botnets) coordinated to launch simultaneous attacks.
- Insider Threats: Malicious actions or inadvertent mistakes perpetrated by individuals within an organization, such as disgruntled employees or careless insiders.
- Insider threats may involve data theft, sabotage, or unintentional exposure of sensitive information.

Example:
- A small business falls victim to a ransomware attack after an employee unknowingly opens a malicious email attachment. The ransomware encrypts critical files on the company’s servers, rendering them inaccessible until a ransom is paid. The incident disrupts business operations and incurs financial losses due to downtime and potential data recovery costs.
Identifying Vulnerabilities
- Software Vulnerabilities: Weaknesses or flaws in software applications or systems that can be exploited by attackers to gain unauthorized access or execute malicious actions.
- Vulnerabilities may result from programming errors, misconfigurations, or outdated software versions.
- Network Vulnerabilities: Weak points in network infrastructure or protocols that can be exploited to compromise data integrity, confidentiality, or availability.
- Vulnerabilities may include unsecured network ports, misconfigured firewalls, or lack of encryption protocols.
- Human Factors: Human error or negligence that inadvertently exposes systems or data to risk, such as using weak passwords, falling for phishing scams, or improperly handling sensitive information.
- Social engineering techniques exploit human vulnerabilities to manipulate individuals into divulging confidential information or performing actions detrimental to security.
Example:
- A multinational corporation discovers a critical vulnerability in its enterprise resource planning (ERP) software that could potentially allow remote attackers to execute arbitrary code on company servers. The vulnerability, caused by insecure default configurations, underscores the importance of regular software updates and security patches to mitigate the risk of exploitation.
Mitigating Cyber Threats and Vulnerabilities
- Patch Management: Regularly update software and firmware to address known vulnerabilities and security flaws.
- User Education and Training: Provide cybersecurity awareness training to employees to recognize and respond to phishing attempts, social engineering tactics, and other cyber threats.
- Access Control: Implement robust authentication mechanisms and access controls to restrict unauthorized access to sensitive data and systems.
- Network Security Measures: Deploy firewalls, intrusion detection/prevention systems, and antivirus software to detect and block malicious activity on networks and endpoints.
- Incident Response Planning: Develop and regularly test incident response plans to effectively mitigate the impact of cyber incidents and facilitate swift recovery.
- Continuous Monitoring: Implement tools and processes for real-time monitoring of network traffic, system logs, and security alerts to detect and respond to potential threats promptly.
Example:
- A financial institution enhances its cybersecurity posture by implementing a multi-layered defense strategy. This includes deploying firewalls to monitor and filter incoming network traffic, conducting regular vulnerability assessments to identify and remediate weaknesses, and providing comprehensive cybersecurity training to employees to bolster awareness and resilience against cyber threats.
By exploring the landscape of cyber threats and vulnerabilities, individuals and organizations can better understand the risks posed by malicious actors and take proactive measures to safeguard their digital assets.
3. Encryption and Cryptography
Encryption and cryptography play pivotal roles in ensuring the confidentiality, integrity, and authenticity of sensitive information transmitted and stored in the digital domain.
In this comprehensive exploration, we’ll delve into the intricacies of encryption and cryptography, unraveling the mechanisms that underpin secure communication and data protection.

Understanding Encryption
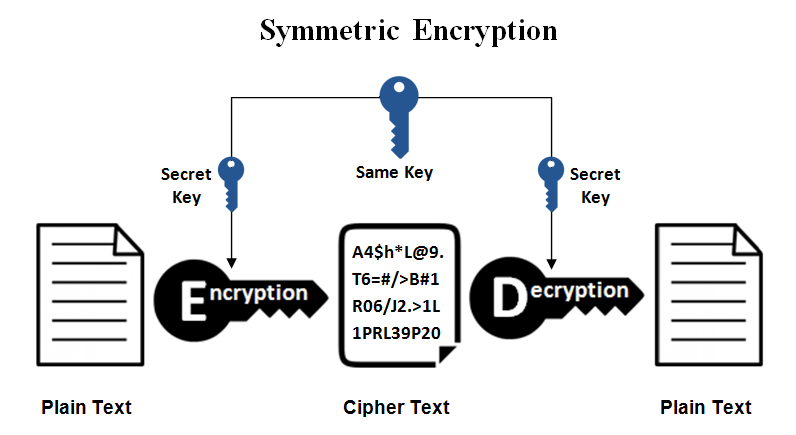
- Definition: Encryption is the process of converting plaintext data into ciphertext using mathematical algorithms and cryptographic keys.
- Components of Encryption:
- Plaintext: The original, unencrypted data that is to be protected.
- Ciphertext: The encrypted form of the plaintext data, rendered unreadable without the corresponding decryption key.
- Encryption Algorithm: Mathematical operations used to transform plaintext into ciphertext.
- Encryption Key: A unique sequence of bits used to encrypt and decrypt data.
- Types of Encryption:
- Symmetric Encryption: Uses a single encryption key for both encryption and decryption.
- Asymmetric Encryption (Public-Key Encryption): Employs a pair of keys – a public key for encryption and a private key for decryption.
Example:
- Alice wishes to send a confidential message to Bob over an insecure communication channel. Using symmetric encryption, Alice encrypts the plaintext message using a shared secret key before transmitting it to Bob. Upon receiving the ciphertext, Bob decrypts it using the same key to recover the original message.
Exploring Cryptographic Techniques
- Symmetric Encryption Algorithms:
- AES (Advanced Encryption Standard): Widely adopted symmetric encryption algorithm known for its efficiency and security.
- DES (Data Encryption Standard): Legacy symmetric encryption algorithm replaced by AES due to security vulnerabilities.
- Asymmetric Encryption Algorithms:
- RSA (Rivest-Shamir-Adleman): Popular asymmetric encryption algorithm based on the difficulty of factoring large prime numbers.
- Elliptic Curve Cryptography (ECC): Utilizes the mathematical properties of elliptic curves for secure key exchange and digital signatures.
Applications of Encryption
- Secure Communication: Encryption ensures the confidentiality and integrity of data transmitted over public networks, such as the internet.
- Data Storage: Encrypted storage solutions protect sensitive data stored on devices, servers, and cloud platforms from unauthorized access.
- Digital Signatures: Cryptographic techniques such as digital signatures verify the authenticity and integrity of digital documents and transactions.
- Secure Transactions: Encryption secures online transactions, including e-commerce purchases, banking transactions, and cryptocurrency transactions.
Example:
- Jane, a customer, completes an online purchase using her credit card on an e-commerce website. Before transmitting the payment details over the internet, the website encrypts the transaction using Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols. This encryption ensures that Jane’s credit card information remains confidential and protected from interception by malicious actors.

Challenges and Considerations
- Key Management: Securely managing encryption keys is critical to maintaining the integrity and confidentiality of encrypted data.
- Performance Impact: Strong encryption algorithms may impose computational overhead, impacting system performance, particularly in resource-constrained environments.
- Regulatory Compliance: Compliance with data protection regulations may require adherence to specific encryption standards and practices, such as GDPR and HIPAA.
Encryption and cryptography serve as indispensable tools in the arsenal of cybersecurity, safeguarding sensitive information from prying eyes and malicious actors.
By harnessing the power of encryption algorithms and cryptographic techniques, individuals and organizations can navigate the digital landscape with confidence, knowing that their data remains secure and protected.
4. Authentication and Access Control
Authentication and access control mechanisms serve as the first line of defense in protecting sensitive data and resources from unauthorized access.
In this comprehensive exploration, we’ll delve into the intricacies of authentication and access control, illuminating the strategies and techniques employed to verify user identities and enforce access privileges.
Understanding Authentication
- Definition: Authentication is the process of verifying the identity of users or entities attempting to access a system or resource.
- Components of Authentication:
- Credentials: Information provided by users to prove their identity, such as usernames, passwords, or biometric data.
- Authentication Factors: Categories of information used to authenticate users, including:
- Knowledge Factor: Something the user knows (e.g., password, PIN).
- Possession Factor: Something the user has (e.g., security token, mobile device).
- Inherence Factor: Something inherent to the user (e.g., fingerprint, retina scan).
- Authentication Methods:
- Single-Factor Authentication (SFA): Relies on a single authentication factor (e.g., password).
- Multi-Factor Authentication (MFA): Requires two or more authentication factors for verification, enhancing security.
Access Control Mechanisms
- Role-Based Access Control (RBAC): Assigns permissions to users based on their roles or responsibilities within an organization.
- Example: An employee’s access privileges are determined by their job title or department, restricting access to sensitive information based on their role.
- Attribute-Based Access Control (ABAC): Grants access based on specific attributes or characteristics of users, resources, and environmental factors.
- Example: Access to confidential documents is granted only to users with a security clearance level above a certain threshold.
- Discretionary Access Control (DAC): Allows users to control access permissions for resources they own, granting or revoking access at their discretion.
- Example: A file owner can specify which users or groups have permission to view, edit, or delete the file.
- Mandatory Access Control (MAC): Enforces access policies based on system-wide rules set by administrators, overriding user discretion.
- Example: Government agencies use MAC to classify and restrict access to classified information based on security clearance levels.
Authentication and Access Control Best Practices
- Strong Password Policies: Enforce password complexity requirements (e.g., minimum length, use of special characters) and regular password rotation to mitigate the risk of unauthorized access.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security beyond passwords, reducing the likelihood of account compromise.
- Least Privilege Principle: Grant users the minimum level of access necessary to perform their duties, limiting the potential impact of unauthorized access.
- User Account Management: Regularly review and update user accounts, removing inactive or unnecessary accounts to minimize security risks.
- Access Monitoring and Auditing: Implement robust logging mechanisms to track user access and detect suspicious activity, facilitating incident response and forensic analysis.
Real-World Examples
- Online Banking Authentication: Banks often implement MFA, requiring customers to provide a combination of passwords, security questions, and one-time codes sent to their mobile devices for secure account access.
- Enterprise Network Access Control: Organizations use RBAC and ABAC to manage employee access to corporate resources, ensuring that sensitive data is only accessible to authorized personnel based on their roles and permissions.
Authentication and access control form the cornerstone of cybersecurity, safeguarding digital assets and resources from unauthorized access and misuse.
By implementing robust authentication methods and access control mechanisms, individuals and organizations can mitigate the risk of data breaches and unauthorized intrusions, bolstering their defenses in an increasingly interconnected world.
5. Network Security Concepts
Network security is paramount in protecting the integrity, confidentiality, and availability of data transmitted over interconnected networks.
In this extensive exploration, we’ll delve into the essential concepts and strategies employed to fortify digital perimeters against cyber threats.
Firewalls: Defending Against Unauthorized Access
- Definition: Firewalls are network security devices that monitor and control incoming and outgoing traffic based on predetermined security rules.
- Types of Firewalls:
- Packet Filtering Firewalls: Examines individual packets of data and applies access control rules based on IP addresses, ports, and protocols.
- Stateful Inspection Firewalls: Tracks the state of active connections and makes decisions based on the context of the traffic, enhancing security.
- Application Layer Firewalls: Operate at the application layer of the OSI model, inspecting and filtering traffic based on application-specific protocols and content.

Intrusion Detection and Prevention Systems (IDPS): Detecting and Mitigating Threats
- Definition: IDPS are security mechanisms designed to detect and respond to malicious activities and security breaches within a network.
- Intrusion Detection Systems (IDS):
- Analyze network traffic and system logs for signs of suspicious activity or known attack patterns.
- Generate alerts or notifications to security personnel upon detection of potential security incidents.
- Intrusion Prevention Systems (IPS):
- Actively block or mitigate detected threats by applying predefined security policies and rules.
- Employ techniques such as packet filtering, protocol validation, and signature-based detection to thwart attacks in real-time.
Virtual Private Networks (VPNs): Securing Remote Connections
- Definition: VPNs establish secure, encrypted tunnels over public networks, enabling remote users to access private networks securely.
- Types of VPNs:
- Remote Access VPNs: Allow individual users to connect to a private network from remote locations using encrypted tunnels.
- Site-to-Site VPNs: Connect multiple geographically distributed networks, enabling secure communication between different locations.
- VPN Protocols:
- IPsec (Internet Protocol Security): Provides secure communication over IP networks by encrypting and authenticating IP packets.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): Establishes secure connections between client devices and VPN servers using cryptographic protocols.
Network Segmentation: Controlling Traffic Flow
- Definition: Network segmentation divides a network into smaller, isolated segments to control the flow of traffic and contain potential security breaches.
- Benefits of Network Segmentation:
- Reduces the attack surface by limiting the scope of potential security incidents.
- Enhances network performance and reliability by isolating traffic and minimizing congestion.
- Segmentation Techniques:
- VLANs (Virtual Local Area Networks): Logical segmentation of network devices into separate broadcast domains, improving network scalability and management.
- Subnetting: Divides a larger network into smaller subnetworks (subnets) based on IP address ranges, facilitating efficient routing and resource allocation.
Examples in Practice
- Corporate Firewall Implementation: A company deploys a firewall at the perimeter of its network to filter incoming and outgoing traffic, blocking unauthorized access attempts and mitigating the risk of malware infections.
- Intrusion Detection System Deployment: An organization installs an IDS to monitor its network traffic for signs of suspicious activity, such as port scans or anomalous traffic patterns. Upon detection, the IDS generates alerts, allowing security analysts to investigate and respond to potential security incidents promptly.
- VPN Usage for Remote Workforce: In response to the rise of remote work, a business establishes a VPN infrastructure to secure remote connections for employees accessing corporate resources from home or remote locations.
Network security concepts form the backbone of cybersecurity, providing essential defenses against a wide range of cyber threats.
By leveraging firewalls, intrusion detection systems, VPNs, and network segmentation techniques, organizations can establish robust defenses to safeguard their digital assets and ensure the integrity and availability of their networks.
6. Incident Response and Disaster Recovery
Incident response and disaster recovery are critical components of cybersecurity, essential for minimizing the impact of security incidents and ensuring business continuity in the face of adversity.
In this comprehensive guide, we’ll explore the intricacies of incident response and disaster recovery, outlining strategies and best practices to mitigate risks and respond effectively to cyber threats.
Incident Response: The First Line of Defense
- Definition: Incident response is a structured approach to addressing and managing security incidents promptly and effectively.
- Key Components of Incident Response:
- Preparation: Establishing incident response plans, policies, and procedures in advance to streamline response efforts.
- Identification: Detecting and categorizing security incidents through continuous monitoring, intrusion detection systems, and security alerts.
- Containment: Isolating and mitigating the impact of security incidents to prevent further damage or unauthorized access.
- Eradication: Removing the root cause of security incidents and implementing corrective measures to prevent recurrence.
- Recovery: Restoring affected systems and data to normal operations while minimizing downtime and disruptions.
- Lessons Learned: Conducting post-incident reviews and analysis to identify areas for improvement and strengthen future response efforts.
Disaster Recovery: Restoring Business Operations
- Definition: Disaster recovery encompasses strategies and processes for restoring IT systems, applications, and data following a disruptive event.
- Key Components of Disaster Recovery:
- Backup and Recovery: Regularly backing up critical data and systems to ensure data integrity and facilitate recovery in the event of data loss or system failure.
- Redundancy and Failover: Implementing redundant systems, infrastructure, and data centers to maintain business continuity and minimize downtime.
- Business Continuity Planning: Developing comprehensive plans and procedures to ensure essential business functions can continue in the event of a disaster or crisis.
- Testing and Validation: Regularly testing disaster recovery plans and procedures through simulated scenarios and tabletop exercises to identify and address gaps.
- Coordination and Communication: Establishing clear lines of communication and coordination among stakeholders, response teams, and external partners to facilitate effective response and recovery efforts.
Best Practices for Incident Response and Disaster Recovery
- Establish Incident Response Teams: Form dedicated incident response teams comprising skilled professionals responsible for coordinating and executing response efforts.
- Develop Incident Response Plans: Create detailed incident response plans outlining roles, responsibilities, escalation procedures, and response workflows.
- Automate Response Processes: Implement automated incident response tools and technologies to facilitate rapid detection, analysis, and containment of security incidents.
- Conduct Regular Training and Drills: Provide ongoing training and awareness programs for incident response team members and stakeholders, including simulated drills and tabletop exercises.
- Engage External Partners: Establish relationships with external partners, such as cybersecurity vendors, legal counsel, and law enforcement agencies, to augment incident response capabilities and resources.
Real-World Examples
- Ransomware Attack Response: A healthcare organization experiences a ransomware attack that encrypts critical patient records and disrupts hospital operations. The incident response team immediately activates the incident response plan, isolates affected systems, and initiates recovery procedures, including restoring data from backups and deploying security patches to prevent further spread of the ransomware.
- Natural Disaster Recovery: A financial institution’s data center suffers damage due to a natural disaster, resulting in the loss of critical infrastructure and services. The disaster recovery team swiftly activates backup systems, reroutes traffic to redundant data centers, and coordinates with external service providers to restore operations and minimize customer impact.
Incident response and disaster recovery are essential pillars of cybersecurity resilience, enabling organizations to effectively manage security incidents and maintain business continuity in the face of unforeseen challenges.
By implementing robust incident response plans, disaster recovery strategies, and best practices, organizations can minimize the impact of security incidents and ensure rapid recovery from disruptions, safeguarding their assets, reputation, and operations.
Stay tuned as we continue to explore essential cybersecurity concepts in the following sections.
Conclusion
Mastering cybersecurity basics is essential in today’s interconnected digital landscape, where the protection of sensitive information and digital assets is paramount.
Throughout this comprehensive guide, we’ve delved into the fundamental concepts that underpin effective cybersecurity practices, empowering individuals and organizations to navigate the complexities of cyberspace with confidence and resilience.
From understanding the significance of cybersecurity fundamentals to exploring the intricacies of encryption, authentication, network security, and incident response, we’ve covered a breadth of essential topics.
By grasping these key concepts, readers have gained insights into the mechanisms and strategies used to safeguard data integrity, confidentiality, and availability, ensuring robust protection against cyber threats.
Moreover, we’ve highlighted real-world examples and best practices to illustrate the practical applications of cybersecurity principles in diverse contexts.
Whether it’s implementing multi-factor authentication to secure online accounts, deploying firewalls and intrusion detection systems to protect network infrastructure, or developing incident response and disaster recovery plans to mitigate the impact of security incidents, the knowledge gained from this guide equips readers with actionable insights to enhance their cybersecurity posture.
In today’s digital age, where cyber threats continue to evolve in sophistication and scale, the importance of mastering cybersecurity basics cannot be overstated.
By fostering a culture of cybersecurity awareness and adopting proactive measures to mitigate risks, individuals and organizations can safeguard their digital assets and maintain trust in the integrity of online interactions.
As technology continues to advance and cyber threats evolve, the journey to mastering cybersecurity basics is ongoing.
It requires continuous learning, adaptation, and vigilance to stay ahead of emerging threats and protect against potential vulnerabilities.
By staying informed, remaining vigilant, and implementing best practices, readers can contribute to a safer and more secure digital ecosystem for themselves and future generations.
In closing, mastering cybersecurity basics is not just about acquiring knowledge; it’s about empowering individuals and organizations to take control of their digital destiny, ensuring that they can navigate the complexities of cyberspace with confidence and resilience.
Together, let’s continue to strive towards a future where cybersecurity is not just a priority but a shared responsibility for all.
If you find this article useful, why not share it with your friends and also leave a nice comment below?
We, at the 9cv9 Research Team, strive to bring the latest and most meaningful data, guides, and statistics to your doorstep.
To get access to top-quality guides, click over to 9cv9 Blog.
If you are keen to find a job or internship, then click on 9cv9 Job Portal now.
People Also Ask
What are the basics of cyber security?
The basics of cybersecurity involve protecting digital systems, networks, and data from cyber threats. This includes implementing measures such as encryption, authentication, access control, and regular software updates to safeguard against unauthorized access, data breaches, and other cyber attacks.
What are the five 5 basic principles of cyber security?
The five basic principles of cybersecurity are confidentiality, integrity, availability, authentication, and non-repudiation. These principles guide efforts to protect sensitive information, ensure data accuracy and accessibility, verify user identities, and establish accountability for actions taken within digital systems.
What are the 5 C’s of cyber security?
The 5 C’s of cybersecurity are Capability, Capacity, Culture, Collaboration, and Coordination. These principles emphasize building strong technical capabilities, fostering a cybersecurity-aware culture, and promoting collaboration and coordination among stakeholders to effectively mitigate cyber threats.






























![Writing A Good CV [6 Tips To Improve Your CV] 6 Tips To Improve Your CV](https://blog.9cv9.com/wp-content/uploads/2020/06/2020-06-02-2-100x70.png)


